Cybage Software interview experience Real time questions & tips from candidates to crack your interview
Software Engineer
Cybage Software
3 rounds | 15 Coding
problems
Interview preparation journey
Preparation
Duration: 4 Months
Topics: Data Structures, Algorithms, Aptitude, Java, Spring Boot, SQL, OOPS
Tip
Tip 1 : Must do Previously asked Interview as well as Online Test Questions.
Tip 2 : Go through all the previous interview experiences from Codestudio and Leetcode.
Tip 3 : Do at-least 2 good projects and you must know every bit of them.
Application process
Where: Campus
Eligibility: Above 7 CGPA
Resume tip
Tip 1 : Have at-least 2 good projects explained in short with all important points covered.
Tip 2 : Every skill must be mentioned.
Tip 3 : Focus on skills, projects and experiences more.
Interview rounds
01
Round
Medium
Face to Face
Duration60 Minutes
Interview date20 May 2019
Coding problem6
This round started with 1 DSA question related to Dynamic Programming and then the interviewer switched to questions revolving around fundamentals of Java and OOPS.
1. Count Ways To Reach The N-th Stairs
Moderate
30m average time
80% success
0/80
Asked in companies



You have been given a number of stairs. Initially, you are at the 0th stair, and you need to reach the Nth stair.
Each time, you can climb either one step or two steps.
You are supposed to return the number of distinct ways you can climb from the 0th step to the Nth step.
Note:
Note: Since the number of ways can be very large, return the answer modulo 1000000007.
Example :
N=3
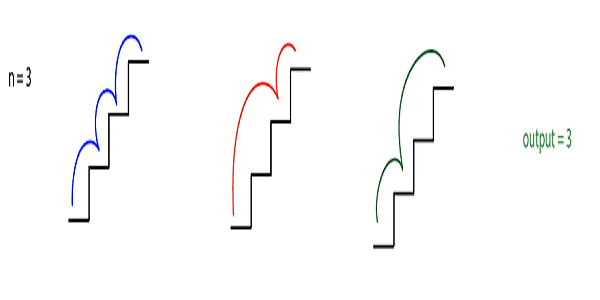
We can climb one step at a time i.e. {(0, 1) ,(1, 2),(2,3)} or we can climb the first two-step and then one step i.e. {(0,2),(1, 3)} or we can climb first one step and then two step i.e. {(0,1), (1,3)}.
Problem approach
Approach (Using DP) :
Our intuition is:
How can we reach “currStep” step in taking one step or two steps:
1) We can take the one-step from (currStep-1)th step or,
We can take the two steps from (currStep-2)th step.
2) So the total number of ways to reach “currStep” will be the sum of the total number of ways to reach at (currStep-
1)th and the total number of ways to reach (currStep-2)th step.
Let dp[currStep] define the total number of ways to reach “currStep” from the 0th. So,
dp[ currStep ] = dp[ currStep-1 ] + dp[ currStep-2 ]
3) The base case will be, If we have 0 stairs to climb then the number of distinct ways to climb will be one (we are
already at Nth stair that’s the way) and if we have only one stair to climb then the number of distinct ways to climb will
be one, i.e. one step from the beginning.
TC : O(N), where ‘N’ is the number of stairs.
SC : O(N)
2. Java Question
What are the various access specifiers in Java?
Problem approach
In Java, access specifiers are the keywords which are used to define the access scope of the method, class, or a
variable. In Java, there are four access specifiers given below.
1) Public : The classes, methods, or variables which are defined as public, can be accessed by any class or method.
2) Protected : Protected can be accessed by the class of the same package, or by the sub-class of this class, or
within the same class.
3) Default : Default are accessible within the package only. By default, all the classes, methods, and variables are of
default scope.
4) Private : The private class, methods, or variables defined as private can be accessed within the class only.
3. Java Question
How many types of memory areas are allocated by JVM?
Problem approach
1) Class(Method) Area : Class Area stores per-class structures such as the runtime constant pool, field, method data,
and the code for methods.
2) Heap : It is the runtime data area in which the memory is allocated to the objects
3) Stack : Java Stack stores frames. It holds local variables and partial results, and plays a part in method invocation
and return. Each thread has a private JVM stack, created at the same time as the thread. A new frame is created
each time a method is invoked. A frame is destroyed when its method invocation completes.
4) Program Counter Register : PC (program counter) register contains the address of the Java virtual machine
instruction currently being executed.
5) Native Method Stack : It contains all the native methods used in the application.
4. Java Question
What is the difference between JDK, JRE, and JVM?
Problem approach
JVM :
JVM is an acronym for Java Virtual Machine; it is an abstract machine which provides the runtime environment in
which Java bytecode can be executed. It is a specification which specifies the working of Java Virtual Machine. Its
implementation has been provided by Oracle and other companies. Its implementation is known as JRE.
JVMs are available for many hardware and software platforms (so JVM is platform dependent). It is a runtime
instance which is created when we run the Java class. There are three notions of the JVM: specification,
implementation, and instance.
JRE :
JRE stands for Java Runtime Environment. It is the implementation of JVM. The Java Runtime Environment is a set
of software tools which are used for developing Java applications. It is used to provide the runtime environment. It is
the implementation of JVM. It physically exists. It contains a set of libraries + other files that JVM uses at runtime.
JDK :
JDK is an acronym for Java Development Kit. It is a software development environment which is used to develop
Java applications and applets. It physically exists. It contains JRE + development tools. JDK is an implementation of
any one of the below given Java Platforms released by Oracle Corporation :
1) Standard Edition Java Platform
2) Enterprise Edition Java Platform
3) Micro Edition Java Platform
5. OOPS Question
What do you mean by data encapsulation?
Problem approach
1) Data Encapsulation is an Object-Oriented Programming concept of hiding the data attributes and their behaviors in
a single unit.
2) It helps developers to follow modularity while developing software by ensuring that each object is independent of
other objects by having its own methods, attributes, and functionalities.
3) It is used for the security of the private properties of an object and hence serves the purpose of data hiding.
6. OOPS Question
Can the static methods be overridden?
Problem approach
1) No. Declaration of static methods having the same signature can be done in the subclass but run time polymorphism can not take place in such cases.
2) Overriding or dynamic polymorphism occurs during the runtime, but the static methods are loaded and looked up at the compile time statically. Hence, these methods cant be overridden.
02
Round
Medium
Face to Face
Duration60 Minutes
Interview date20 May 2019
Coding problem8
In this round, the interviewer first started asking questions related to Java and Spring Boot and then he switched to Hibernate. The interview however ended with the interviewer asking me some basic queries related to SQL.
1. Spring Boot Question
What is dependency Injection?
Problem approach
The process of injecting dependent bean objects into target bean objects is called dependency injection.
1) Setter Injection : The IOC container will inject the dependent bean object into the target bean object by calling the
setter method.
2) Constructor Injection : The IOC container will inject the dependent bean object into the target bean object by calling
the target bean constructor.
3) Field Injection : The IOC container will inject the dependent bean object into the target bean object by Reflection
API.
2. Spring Boot Question
What is the purpose of using @ComponentScan in the class files?
Problem approach
Spring Boot application scans all the beans and package declarations when the application initializes. You need to
add the @ComponentScan annotation for your class file to scan your components added to your project.
3. Spring Boot Question
Can we override or replace the Embedded tomcat server in Spring Boot?
Problem approach
Yes, we can replace the Embedded Tomcat server with any server by using the Starter dependency in the
pom.xml file. Like you can use spring-boot-starter-jetty as a dependency for using a jetty server in your project.
4. Spring Boot Question
What is the starter dependency of the Spring boot module?
Problem approach
Spring boot provides numbers of starter dependency, here are the most commonly used -
1) Data JPA starter.
2) Test Starter.
3) Security starter.
4) Web starter.
5) Mail starter.
6) Thymeleaf starter.
5. Hibernate Question
What is hibernate caching?
Problem approach
Hibernate caching is the strategy for improving the application performance by pooling objects in the cache so that
the queries are executed faster. Hibernate caching is particularly useful when fetching the same data that is executed
multiple times. Rather than hitting the database, we can just access the data from the cache. This results in reduced
throughput time of the application.
Types of Hibernate Caching
First Level Cache :
1) This level is enabled by default.
2) The first level cache resides in the hibernate session object.
3) Since it belongs to the session object, the scope of the data stored here will not be available to the entire
application as an application can make use of multiple session objects.
Second Level Cache :
1) Second level cache resides in the SessionFactory object and due to this, the data is accessible by the entire
application.
2) This is not available by default. It has to be enabled explicitly.
3) EH (Easy Hibernate) Cache, Swarm Cache, OS Cache, JBoss Cache are some example cache providers.
6. Hibernate Question
What are the concurrency strategies available in hibernate?
Problem approach
Concurrency strategies are the mediators responsible for storing and retrieving items from the cache. While enabling
second-level cache, it is the responsibility of the developer to provide what strategy is to be implemented to decide for
each persistent class and collection.
Following are the concurrency strategies that are used:
1) Transactional: This is used in cases of updating data that most likely causes stale data and this prevention is most
critical to the application.
2) Read-Only: This is used when we don't want the data to be modified and can be used for reference data only.
3) Read-Write: Here, data is mostly read and is used when the prevention of stale data is of critical importance.
4) Non-strict-Read-Write: Using this strategy will ensure that there wouldn't be any consistency between the database
and cache. This strategy can be used when the data can be modified and stale data is not of critical concern.
7. SQL Question
Write a query that joins two tables A and B having common attribute ID and selects records(ID_NAME) that have
matching ID values in both tables .
Problem approach
SELECT A.ID_Name, B.ID_Name
FROM A
INNER JOIN B ON A.ID=B.ID;
8. SQL Question
Given an Employee Table, find the Nth highest salary from it.
Problem approach
CREATE FUNCTION getNthHighestSalary(N INT) RETURNS INT
BEGIN
DECLARE M INT;
SET M=N-1;
RETURN (
SELECT DISTINCT Salary FROM Employee ORDER BY Salary DESC LIMIT M, 1
);
END
03
Round
Easy
HR Round
Duration30 Minutes
Interview date20 May 2019
Coding problem1
This is a cultural fitment testing round. HR was very frank and asked standard questions. Then we discussed about my
role.
1. Basic HR Question
Tell me something not there in your resume.
Problem approach
If you get this question, it's an opportunity to choose the most compelling information to share that is not obvious from
your resume.
Example :
Strength -> I believe that my greatest strength is the ability to solve problems quickly and efficiently, which makes me
unique from others.
Ability to handle Pressure -> I enjoy working under pressure because I believe it helps me grow and become more
efficient.
Tip : Emphasize why you were inspired to apply for the job. You can also explain that you are willing to invest a great
deal of energy if hired.
These are generally very open ended questions and are asked to test how quick wit a candidate is. So there is
nothing to worry about if you have a good command over your communication skills and you are able to propagate
your thoughts well to the interviewer.

Here's your problem of the day
Solving this problem will increase your chance to get selected in this company
Skill covered: Programming
What is the purpose of the return keyword?
Choose another skill to practice
Similar interview experiences
React developer
3 rounds | 17 problems
Interviewed by Cybage Software
1315 views
0 comments
0 upvotes
SDE - 1
3 rounds | 7 problems
Interviewed by OYO
4782 views
0 comments
0 upvotes
SDE - 1
2 rounds | 5 problems
Interviewed by Meesho
6543 views
0 comments
0 upvotes
SDE - 1
3 rounds | 9 problems
Interviewed by Salesforce
3567 views
0 comments
0 upvotes
Companies with similar interview experiences
Software Engineer
4 rounds | 1 problems
Interviewed by Newgen Software
3238 views
2 comments
0 upvotes
Software Engineer
3 rounds | 6 problems
Interviewed by HashedIn
2621 views
0 comments
0 upvotes
Software Engineer
2 rounds | 2 problems
Interviewed by Ernst & Young (EY)
0 views
0 comments
0 upvotes










