Gainsight interview experience Real time questions & tips from candidates to crack your interview
Software Engineer
Gainsight
2 rounds | 5 Coding
problems
Interview preparation journey
Preparation
Duration: 5 months
Topics: Data Structures, Algorithms, Java, Springboot, System Design, Aptitude, OOPS
Tip
Tip 1 : Must do Previously asked Interview as well as Online Test Questions.
Tip 2 : Go through all the previous interview experiences from Codestudio and Leetcode.
Tip 3 : Do at-least 2 good projects and you must know every bit of them.
Application process
Where: Referral
Eligibility: Above 7 CGPA
Resume tip
Tip 1 : Have at-least 2 good projects explained in short with all important points covered.
Tip 2 : Every skill must be mentioned.
Tip 3 : Focus on skills, projects and experiences more.
Interview rounds
01
Round
Medium
Video Call
Duration60 minutes
Interview date13 Aug 2020
Coding problem2
Technical Round with questions on DSA.
1. Boundary Traversal of Binary Tree
Hard
20m average time
85% success
0/120
Asked in companies



You are given a binary tree having 'n' nodes.
The boundary nodes of a binary tree include the nodes from the left and right boundaries and the leaf nodes, each node considered once.
Figure out the boundary nodes of this binary tree in an Anti-Clockwise direction starting from the root node.
Example :
Input: Consider the binary tree A as shown in the figure:
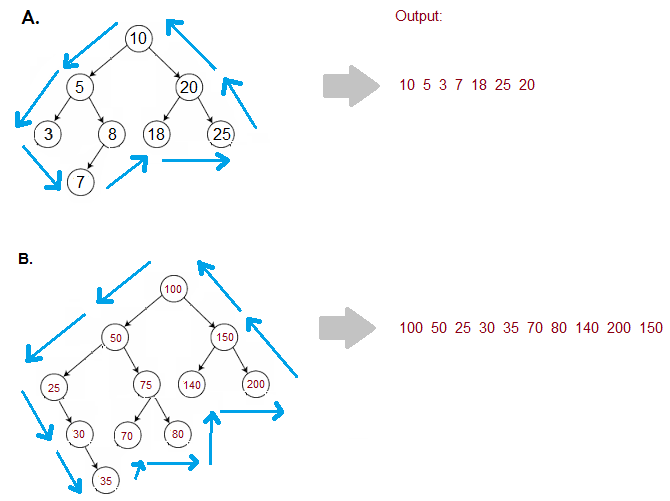
Output: [10, 5, 3, 7, 18, 25, 20]
Explanation: As shown in the figure
The nodes on the left boundary are [10, 5, 3]
The nodes on the right boundary are [10, 20, 25]
The leaf nodes are [3, 7, 18, 25].
Please note that nodes 3 and 25 appear in two places but are considered once.
Problem approach
The idea is to split the problem into 3 parts:
• Print the left boundary in a top-down manner.
• Print the leaf nodes in the same order as in the inorder traversal.
• Print the right boundary in a bottom-up manner.
Time Complexity : O(N)
Two edge cases need to be taken care of :
1. Both the left boundary and the right boundary traversal prints the root node. To avoid this, print the root node first and then perform left and right boundary traversal on left and right child respectively.
2. The leftmost and the rightmost node of the binary tree are leaf nodes. They will get printed while performing the left boundary and the right boundary traversal while printing the leaf nodes. To avoid it, exclude the leaf nodes while doing the left boundary and the right boundary traversal.
2. Spreading Smoke
Easy
26m average time
75% success
0/40
Asked in companies


You are given a room as a grid of 1’s and 0’s. 1 indicating blocked cell and 0 indicating a free cell. There is a bomb in the X'th row from the top and Y’th column from the left. The bomb went off and smoke was starting to spread. In one sec smoke can spread to an adjacent cell if the adjacent cell has 0 in it. The bomb is always at the free cell.
Find the minimum time for the smoke to spread across all the reachable cells. A cell is reachable from another cell if you can travel from one cell to another via cells containing 0’s.
Cells are adjacent if they share a common edge.
For example:
GRID=[[1,1,0,1],
[1,0,0,0],
[1,1,0,1]]
X,Y= (2, 3)
ANS = 2
In 1’st sec smoke will spread to (1, 3), (3, 3), (2, 2), (2, 4)
In 2’nd sec smoke will spread to (2, 1)
Problem approach
BFS can be used to find the cell which is reachable from the bomb and farthest from the bomb.
Start the BFS from the location at expanding to the four adjacent cells if there are not visited so far.
For each cell, also maintain the smallest distance from the bomb.
Algorithm:
1. Initialize Distace[N][M] to infinity.
2. Initialise Distace[X][Y] to 1.
3. Queue = [(X, Y)] : This queue stores all the unprocessed cells, we will pop a cell from the queue and try to move to an adjacent cell
4. Initially, Ans = -1. Ans stores the final answer
5. While (size of Queue > 0)
a, b = Queue.pop()
ans=Distance[a][b]
For all not visited adjacent cells
If Grid[a][b]==0 and Distance[a][b]== infinity
Try to visit all the adjacent cells if the distance of adjacent cells is infinity then this cell is not visited yet
Distance[adjacent-x][adjacent-y]=Distance[a][b]+1
Queue.push((ad-x,ad-y)) : Addd the adjacent the cell to queue
Time Complexity : O(N*M) where ‘N’, ‘M’, is the dimensions of the room.
Space Complexity : O(N*M) where ‘N’, ‘M’, is the dimensions of the room.
02
Round
Medium
Video Call
Duration60 minutes
Interview date13 Aug 2020
Coding problem3
Technical Round with questions on Java, spring and System Design.
1. System Design Question
Design book my show.
Problem approach
Tip 1 : Firstly, remember that the system design round is extremely open-ended and there’s no such thing as a standard answer. Even for the same question, you’ll have a totally different discussion with different interviewers.
Tip 2 : Before you jump into the solution always clarify all the assumptions you’re making at the beginning of the interview. Ask questions to identify the scope of the system. This will clear the initial doubt, and you will get to know what are the specific detail interviewer wants to consider in this service.
Tip 3 : Design your structure and functions according to the requirements and try to convey your thoughts properly to the interviewer so that you do not mess up while implementing the idea .
2. Spring Boot Question
What is Inversion of Control in Spring?
Problem approach
In traditional programming, the flow of the business logic is determined by objects that are statically assigned to one another. With inversion of control, the flow depends on the object graph that is instantiated by the assembler and is made possible by object interactions being defined through abstractions. The binding process is achieved through dependency injection, although some argue that the use of a service locator also provides inversion of control.
Inversion of control as a design guideline serves the following purposes :
There is a decoupling of the execution of a certain task from implementation.
Every module can focus on what it is designed for.
Modules make no assumptions about what other systems do but rely on their contracts.
Replacing modules has no side effect on other modules.
3. Design Pattern Question
Command Design Pattern
Problem approach
The command pattern is a behavioral design pattern and is part of the GoF‘s formal list of design patterns. Simply put, the pattern intends to encapsulate in an object all the data required for performing a given action (command), including what method to call, the method's arguments, and the object to which the method belongs.
This model allows us to decouple objects that produce the commands from their consumers, so that's why the pattern is commonly known as the producer-consumer pattern.

Here's your problem of the day
Solving this problem will increase your chance to get selected in this company
Skill covered: Programming
What is the purpose of the return keyword?
Choose another skill to practice
Similar interview experiences
Associate Software Engineer
6 rounds | 4 problems
Interviewed by Gainsight
2577 views
0 comments
0 upvotes
SDE - 1
3 rounds | 8 problems
Interviewed by Gainsight
845 views
0 comments
0 upvotes
SDE - 1
2 rounds | 5 problems
Interviewed by Gainsight
720 views
0 comments
0 upvotes
SDE - 1
3 rounds | 9 problems
Interviewed by Salesforce
3567 views
0 comments
0 upvotes
Companies with similar interview experiences
Software Engineer
3 rounds | 7 problems
Interviewed by Optum
7923 views
1 comments
0 upvotes
Software Engineer
5 rounds | 5 problems
Interviewed by Microsoft
10070 views
1 comments
0 upvotes
Software Engineer
2 rounds | 4 problems
Interviewed by Amazon
4395 views
1 comments
0 upvotes







